
Windows Access Tokens An access token is an object that describes the security context of a process or thread. the information in a token includes the identity and privileges of the user account associated with the process or thread. when a user logs on, the system verifies the user's password by comparing it with information stored in a security database. if the password is authenticated, the system produces an. When the client requests an access token, the microsoft identity platform also returns some metadata about the access token for the consumption of the application. this information includes the expiry time of the access token and the scopes for which it's valid.
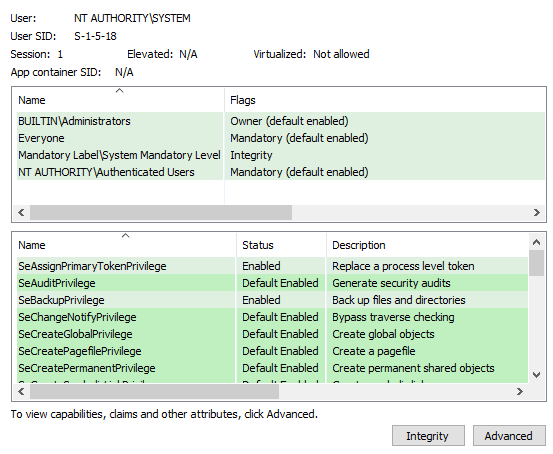
Windows Access Tokens Getting System And Demystifying Potato Exploits How can i properly assign the new token to windows credential ? i did the same thing in macos : put the token in the keychain access and it works, no more filling user pass manually. in windows 10. In windows, an access token is represented by the system object of type token. an access token is generated by the logon service when a user logs on to the system and the credentials provided by the user are authenticated against the authentication database. Windows access token manipulation attacks are well known and abused from an offensive perspective, but rely on an extensive body of arcane windows security internals. in this blog post, we demystify h. So what are windows access tokens? to cite msdn: an access token is an object that describes the security context of a process or thread. the information in a token includes the identity and privileges of the user account associated with the process or thread. when a user logs on […] the system produces an access token.
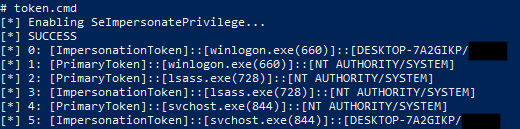
Windows Access Tokens Getting System And Demystifying Potato Exploits Windows access token manipulation attacks are well known and abused from an offensive perspective, but rely on an extensive body of arcane windows security internals. in this blog post, we demystify h. So what are windows access tokens? to cite msdn: an access token is an object that describes the security context of a process or thread. the information in a token includes the identity and privileges of the user account associated with the process or thread. when a user logs on […] the system produces an access token. What are access tokens? every system user who logs in is assigned an access token containing security details for their session. when a user logs in, the system generates an access token for them. each process initiated on behalf of the user is equipped with a duplicate of this access token. this token serves to identify the user, their associated groups, and their granted privileges. Windows: access token when a user logs on, windows creates an access token for this user. it is used to store a user's identity and privileges.
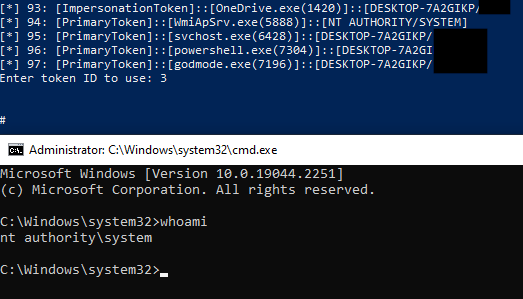
Windows Access Tokens Getting System And Demystifying Potato Exploits What are access tokens? every system user who logs in is assigned an access token containing security details for their session. when a user logs in, the system generates an access token for them. each process initiated on behalf of the user is equipped with a duplicate of this access token. this token serves to identify the user, their associated groups, and their granted privileges. Windows: access token when a user logs on, windows creates an access token for this user. it is used to store a user's identity and privileges.

Access Tokens Memos